Safe, the developer of the SafeWallet multisignature product used by Bybit, has released a short post-mortem update explaining the root cause of the recent Bybit hack — a compromised developer machine. The announcement prompted a critical response from Binance co-founder Changpeng “CZ” Zhao.
According to Safe, the forensic review of the Bybit hack did not find vulnerabilities in the Safe smart contracts or the code of its front end portal and services responsible for the $1.4 billion cybersecurity incident.
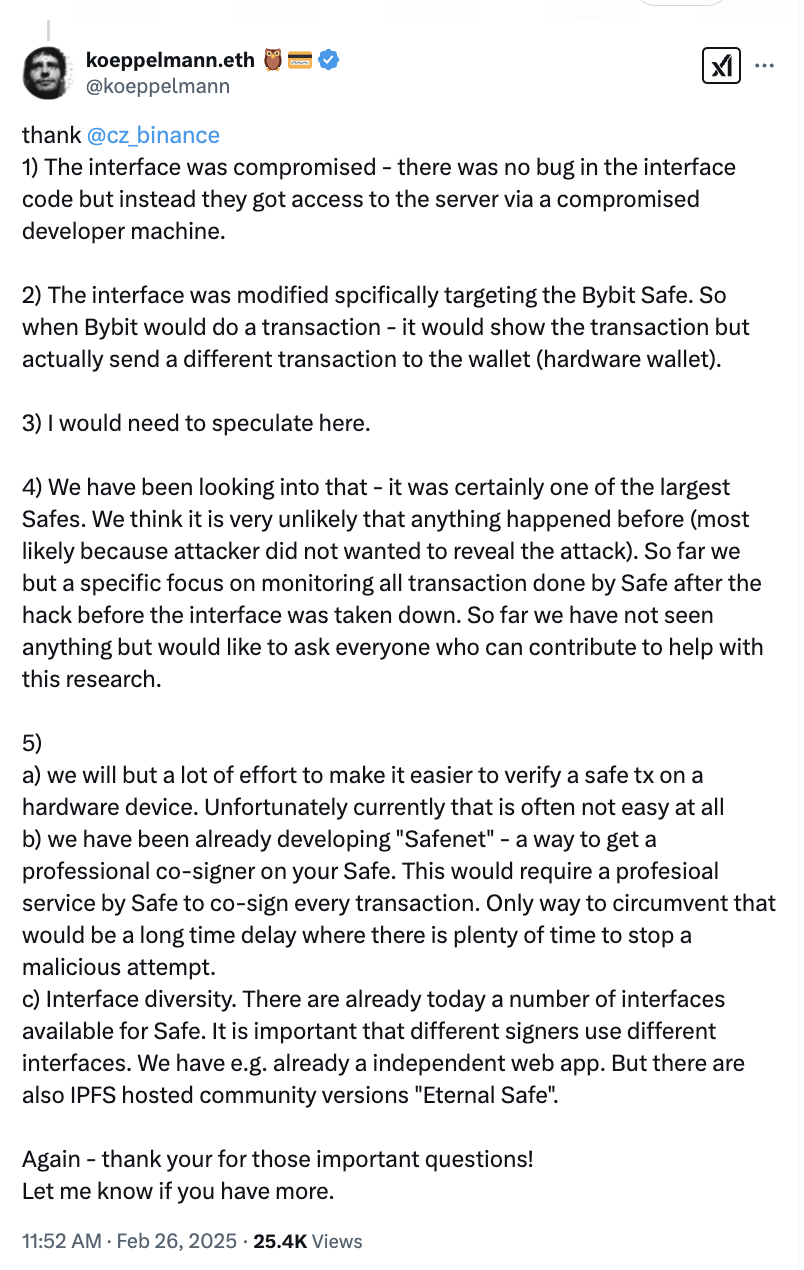
Martin Köppelmann, the co-founder of the Gnosis blockchain network, which developed Safe, noted that the compromised machine was modified to target the Bybit Safe and divert the transactions to a different hardware wallet.
“This update from Safe is not that great. It uses vague language to brush over the issues,” Zhao wrote in a Feb. 26 X post. Zhao also asked for clarification on the compromised developer machines, how the hackers tricked multiple signers into signing the transaction, how a developer machine accessed Bybit’s systems, and why the hackers did not target other addresses.
Source: Changpeng Zhao
Köppelmann added that he could only speculate about how the hackers pushed the fraudulent transactions past multiple signers and theorized that the threat actors did not target other addresses to prevent discovery and detection.
A forensic review conducted by Sygnia and Verichains revealed on Feb. 26 that “the credentials of a Safe developer were compromised […] which allowed the attacker to gain unauthorized access to the Safe(Wallet) infrastructure and totally deceive signers into approving a malicious transaction.”
Source: Martin Köppelmann
Related: Bybit CEO declares ‘war against Lazarus’ after $1.4B hack
Lazarus Group launders funds stolen from Bybit hack
Onchain data shows the Lazarus Group has transferred 45,900 Ether (ETH), valued at approximately $113 million during the last 24 hours.
This brings the total amount of funds laundered at the time of this writing to over 135,000 ETH, valued at roughly $335 million.
According to analyst EmberCN, the infamous hacking group will likely have “cleaned up” the funds within 8-10 days.
Bybit and blockchain analytics firm Elliptic have tracked the stolen crypto to over 11,000 wallets controlled by the Lazarus Group.
Elliptic also published a data feed of addresses associated with the infamous hacker group to help market participants stay clear of those wallet addresses and help prevent money laundering.
Magazine: Lazarus Group’s favorite exploit revealed — Crypto hacks analysis