Artificial Intelligence (AI) is rapidly transforming cybersecurity, playing a dual role by defending digital assets and enabling sophisticated cyberattacks. While AI-powered tools are improving online security, hackers are also using them to steal digital assets. This has become a big concern in the crypto world, where security is already a major challenge.
These bots can scan for weaknesses, launch attacks quickly, and even adjust their tactics to bypass security measures. Because they operate 24/7 without human intervention, they can steal large amounts of crypto before being detected.
This raises a critical question: How are AI-driven threats evolving, and what steps can users take to protect their crypto assets?
The Rise of AI in Cybercrime
Cybercriminals are adopting AI to enhance the scale, speed, and effectiveness of their attacks. AI enables attackers to automate complex tasks, analyze vast amounts of data, and adapt to security measures in real-time.
Automating Phishing and Social Engineering
AI has completely changed how phishing and social engineering attacks work, making them more convincing, targeted, and harder to detect.
AI can study massive amounts of human communication data to create scam emails that look almost identical to real ones. In December 2023, hackers tricked an Activision HR employee using a fake SMS message that looked like an official company alert. The message, titled “Employment Status: Under Review,” asked employees to reply with a two-factor authentication (2FA) code.
One person fell for it, allowing hackers to control a high-level user account and posted a message in Activision’s general Slack channel. This gave them access to internal documents, including release schedules for Call of Duty 2023 and Call of Duty 2024.
- Deepfake Impersonations
Cybercriminals now use AI to create deepfake videos and voice recordings to impersonate trusted people. Fake videos of Elon Musk have been used in scams to lure people into fraudulent investments.
In September 2024, scammers hosted a live-streamed event featuring a deepfaked Elon Musk, which attracted viewers and resulted in approximately $50,000 in fraudulent investments within two hours.
Attackers deploy AI-driven chatbots to engage with victims in real time, pretending to be customer support agents or other trusted contacts. In a notable incident, cybercriminals employed an AI-driven chatbot to deceive victims into divulging personal information.
The attackers crafted a chatbot that mimicked legitimate customer support, guiding users through a series of prompts to collect sensitive data such as names, addresses, passport numbers, and payment details.
AI in Ransomware and Data Breaches
AI is also being used to enhance cyberattacks on large corporations, helping attackers find vulnerabilities and launch highly effective ransomware attacks. In January 2023, Yum! Brands, the company behind KFC, Pizza Hut, and Taco Bell, was hit by a ransomware attack that disrupted its IT systems.
To contain the attack, the company quickly took some systems offline and increased security monitoring. As a result, about 300 restaurants in the UK had to close for a day. At first, it seemed that only company data was affected, but investigations found that hackers also accessed employees’ names, driver’s license numbers, and other sensitive details.
How AI Bots Steal Cryptocurrency
Artificial Intelligence is increasingly being exploited by cybercriminals to steal cryptocurrency through various sophisticated methods. Below are some of the prominent techniques:
Automated Trading Bot Exploits
Malicious actors develop AI-driven trading bots that manipulate cryptocurrency markets and exploit platform vulnerabilities. One common scam involves AI-powered Maximal Extractable Value (MEV) bots. Fraudsters market these bots as automated tools that exploit market inefficiencies for guaranteed profits.
To appear legitimate, scammers provide victims with access to Solidity code containing technical terms like “ConnectFastestNode”, “getMemPoolDepth”, and “SearchProfitability”. However, deeper inspection reveals hidden functions—such as “search”—that secretly transfer funds to the scammer’s wallet instead of generating profits.
AI-Driven Phishing Attacks
Cybercriminals are using AI to make phishing campaigns more convincing, generating realistic messages that closely mimic legitimate cryptocurrency platforms.
In early 2024, an AI-driven phishing attack targeted Coinbase users, tricking them into losing nearly $65 million. Scammers used stolen personal data to make their fraudulent emails seem authentic, warning users of fake security breaches. Posing as Coinbase, they urged victims to transfer funds to a so-called “secure” Coinbase Wallet and whitelist specific addresses, ultimately redirecting money to the scammers.
Malware and Keyloggers
AI-powered malware has become more advanced at stealing private keys and seed phrases from cryptocurrency users. In August 2022, a sophisticated malware strain called Infostealer Luca Stealer was suspected of being used in an attack on the Solana blockchain.
This AI-enhanced malware recorded keystrokes and clipboard data, allowing hackers to steal seed phrases and private keys when users copied and pasted them into crypto wallets. The attack resulted in approximately $7 million in stolen cryptocurrencies from around 8,000 wallets. This incident highlights how AI-powered malware can efficiently target and drain digital assets, posing a growing threat to crypto users.
Smart Contract Exploits
AI algorithms can analyze DeFi protocols to identify and exploit vulnerabilities in smart contracts. By automating vulnerability detection, AI enables attackers to swiftly locate and exploit weaknesses before they are patched. This poses significant risks to DeFi platforms, where smart contract integrity is crucial for security.
In 2024, there were eight reported reentrancy attacks, leading to total losses of around $30 million. Notably, the Penpie protocol suffered the largest reentrancy attack of that year. Similarly, in July 2023, EraLend, a lending protocol on the zkSync blockchain, experienced a reentrancy attack resulting in a loss of $3.4 million. The attacker exploited a read-only reentrancy vulnerability, allowing repeated calls within a single transaction to drain funds.
Strategies to Protect Crypto Holdings from AI Attacks
As AI-driven threats become more advanced, securing your cryptocurrency holdings requires a multi-layered approach. Follow the below steps to reduce risks of losing your assets to cybercriminals.
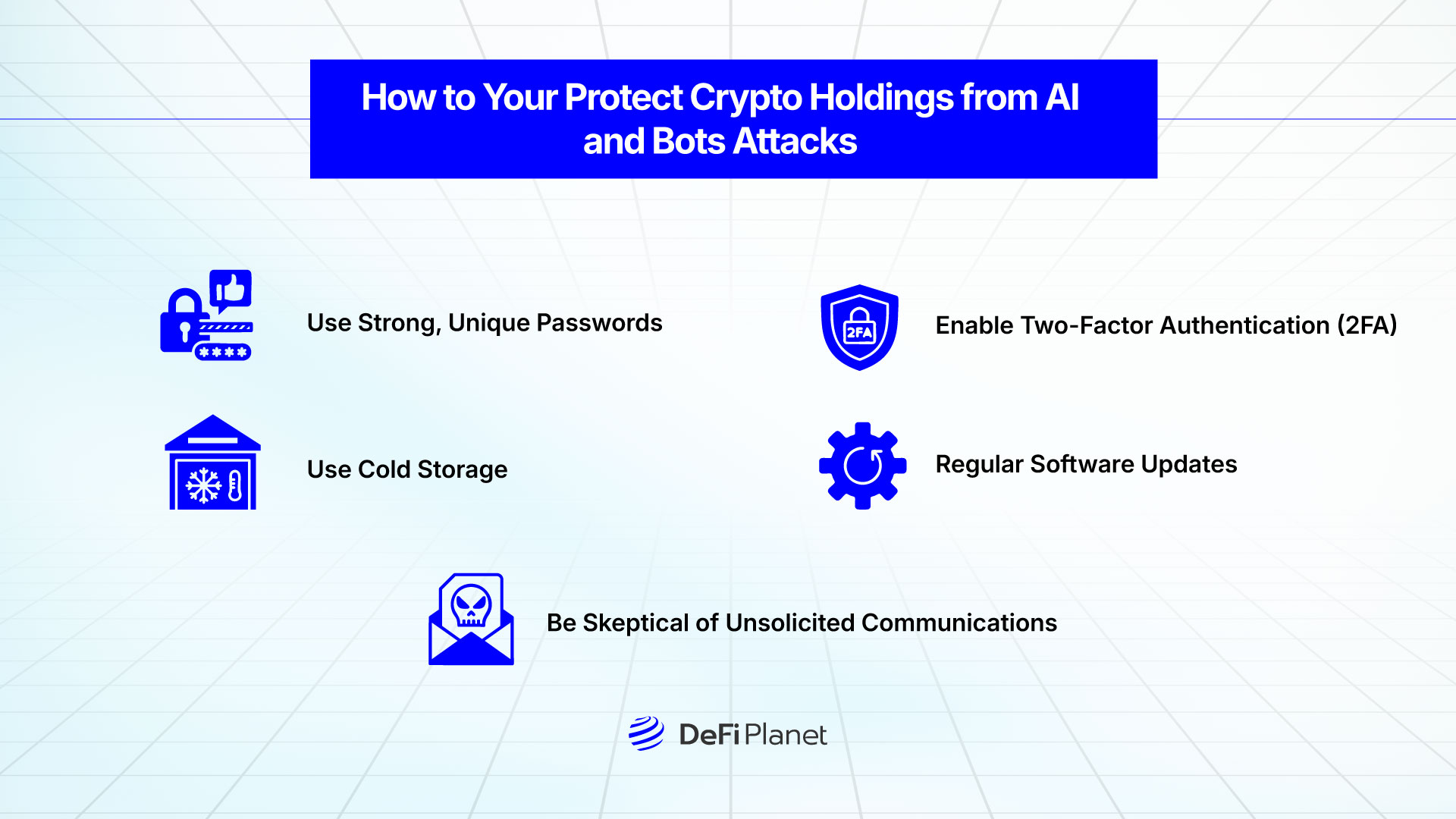
Strengthening Personal Security
- Use Strong, Unique Passwords: Create passwords that combine uppercase and lowercase letters, numbers, and special symbols. Avoid using easily guessable words or personal information. A password manager can help generate and store secure passwords to prevent reuse across different accounts.
- Enable Two-Factor Authentication (2FA): Activate 2FA on all crypto-related accounts to add an extra layer of protection. Use authenticator apps like Google Authenticator or hardware security keys instead of SMS-based 2FA, which can be vulnerable to SIM-swapping attacks.
- Utilize Cold Storage: Store the majority of your cryptocurrency in offline wallets (cold storage) to minimize exposure to online threats. Hardware wallets like Ledger or Trezor provide a secure way to keep private keys offline, reducing the risk of hacks and malware attacks.
- Regular Software Updates: Keep wallet software, exchanges, and security tools up to date. Hackers often exploit outdated software vulnerabilities, so enabling automatic updates or setting reminders for manual updates is crucial for security.
Avoiding AI-Enhanced Phishing
- Be Skeptical of Unsolicited Communications: Exercise caution with unexpected messages, emails, or social media DMs that request sensitive information or urge immediate action. Cybercriminals use AI to craft convincing messages that mimic official communication from crypto platforms and exchanges.
- Verify Authenticity: Always check the legitimacy of communications by contacting organizations directly through official channels. Instead of clicking on links in emails or messages, visit the company’s website manually or use bookmarked links. Scammers often use slight variations of domain names (e.g., “crypto-exchange.com” vs. “cryptoexchánge.com”) to trick users.
- Educate Yourself: Stay informed about the latest phishing tactics by following trusted cybersecurity resources and participating in online security awareness programs. Many exchanges and crypto platforms provide educational materials to help users recognize evolving phishing techniques.
Using AI for Defense
- AI-Powered Threat Detection: Crypto exchanges and security firms use AI-driven systems to analyze transaction patterns and detect suspicious activities. These tools can flag anomalies, such as sudden large withdrawals or transactions from unusual locations, helping prevent fraud.
- Automated Response Mechanisms: AI security systems can respond to potential threats in real-time by temporarily freezing suspicious accounts, blocking unauthorized withdrawals, or sending alerts for verification. Users should enable account activity notifications to stay aware of any unusual activity.
- Continuous Monitoring: AI-powered monitoring tools can scan for security breaches across wallets, smart contracts, and exchanges. They can identify compromised credentials, leaked private keys, or suspicious addresses in real time, allowing users to take swift action before funds are lost.
With these strategies, users and platforms can prevent AI-driven cyber threats and ensure the safety of their crypto assets in an increasingly complex and automated threat space.
Final Thoughts
As AI-driven cyber threats continue to evolve, the question remains: Can AI security measures keep pace with these sophisticated attacks? While AI-powered security tools are becoming more advanced, cybercriminals are also leveraging AI to develop increasingly complex exploits, making this an ongoing arms race.
AI-driven security solutions, such as fraud detection algorithms, real-time threat intelligence, and automated response systems, provide a strong defense against AI-enhanced cybercrime. However, no security measure is foolproof. Hackers continuously adapt, finding new vulnerabilities to exploit, which means security teams must remain proactive, updating defenses and improving AI models to counter emerging threats.
Ultimately, the battle between AI-driven crime and AI-enhanced security is a continuous cycle of innovation on both sides. Users, businesses, and crypto platforms must stay informed and implement robust security practices, combining AI-driven defenses with human vigilance. The future of crypto security will depend on collaboration between technology providers, researchers, and regulators to create a resilient ecosystem that can withstand the ever-changing threats.
Disclaimer: This article is intended solely for informational purposes and should not be considered trading or investment advice. Nothing herein should be construed as financial, legal, or tax advice. Trading or investing in cryptocurrencies carries a considerable risk of financial loss. Always conduct due diligence.
If you would like to read more articles like this, visit DeFi Planet and follow us on Twitter, LinkedIn, Facebook, Instagram, and CoinMarketCap Community.
Take control of your crypto portfolio with MARKETS PRO, DeFi Planet’s suite of analytics tools.”

